Information security |
Basic approach
In light of the business impact of cyber attacks, system down, and information leaks, the IDEC Group recognizes information security risks as risks directly related to management, and has established the “Information Security Basic Policy” to raise employee awareness and take measures against information security-related risks.
We have also established a management system for information security, and are working to ensure the effectiveness of information security and protect our information assets by continuously improving our basic policy, the various internal rules and procedures formulated based on it, and information security.
Management system
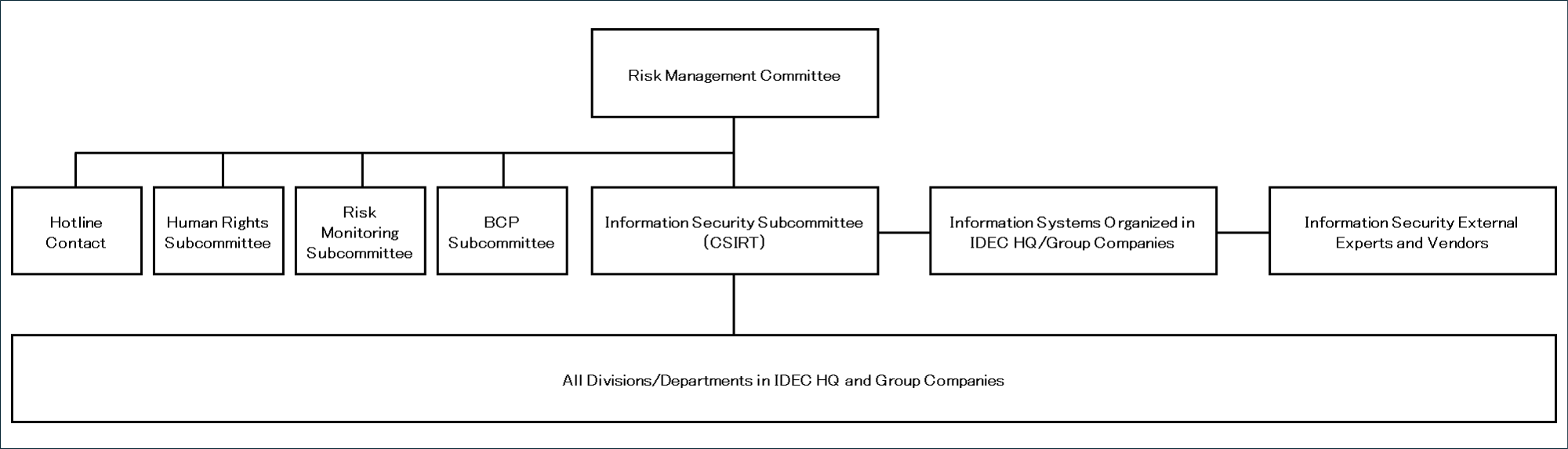
The Information Security Subcommittee was established within the Risk Management Committee, a specialized committee of the Sustainability Committee, to oversee information security management for the entire IDEC Group. The Information Security Subcommittee identifies the information assets of the entire IDEC Group and conducts risk assessment. Based on the results of these assessments, the subcommittee works with the various information security management organizations of each IDEC Group company and their supervisors on a global basis.
We are also working to raise security awareness through education and enlightenment activities for all employees, and have established a reporting system to ensure prompt response and damage minimization in the event of incidents such as cyber attacks and information leaks.
Information security measures
To reduce information security-related risks, the IDEC Group works continuously to assess the internal and external environment in relation to information security, with an emphasis on strengthening countermeasures.
We work to prevent information security incidents by ensuring that management and all employees understand the importance of information security, not only through technical measures, but also through organizational measures such as rule development, education, enlightenment, and training, etc.
In the event of an information security incident, a CSIRT will be formed under the supervision of the chairperson of the Information Security Subcommittee to collect information and report promptly to management, and an emergency task force will be established. Countermeasures are determined and implemented taking into account the impact on stakeholders, including customers and suppliers, as well as those within the Group.
Education and Training
It is important that each and every employee understands the importance of information security and takes defensive action.
We regularly provide information security education (e-Learning) for all employees, and also conduct training on targeted email attacks to raise awareness.
| Information security e-Learning attendance in FY2025 (Japan) | |||
| Period | Theme | Number of attendees | Training attendance rate |
| May 2024 | Malware | 1,269 | 100% |
| July 2024 | Physical Security | 1,254 | 100% |
| September 2024 | Multi-factor authentication | 1,239 | 100% |
| November 2024 | AI | 1,222 | 100% |
Protection of Private Information
The IDEC Group recognizes that it is its important social responsibility to properly protect and handle information that can identify specific individuals, such as the names, addresses, and email addresses of customers, suppliers, and business partners, and manages the information it obtains in accordance with its Privacy Policy.